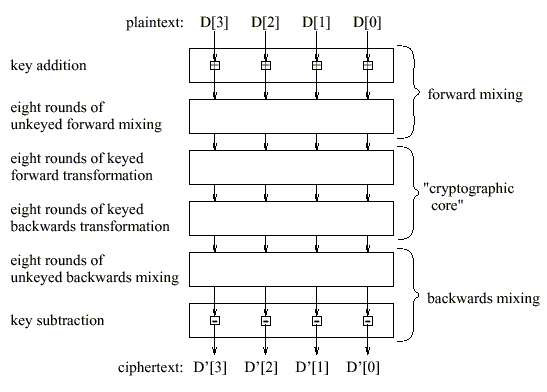
Figure 1: High-level structure of the cipher [MarsIBM99]
Reto Galli
ECE 575 Project - Winter 2000
The goal of this project is the analyzes of MARS encryption algorithm and point out some advantages of this algorithms compared to the other candidates for AES. Further a demo program based on the c-code that was published by NIST on February, 18th 2000 shows how the algorithm works.

Figure 1: High-level structure of the cipher [MarsIBM99]
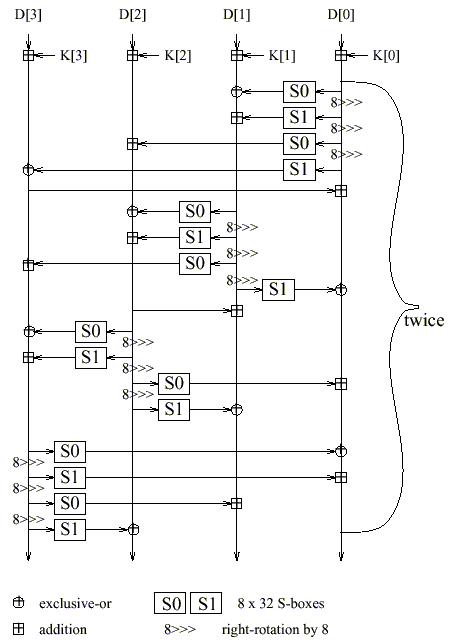
Figure 2: Structure of the forward mixing phase [MarsIBM99]
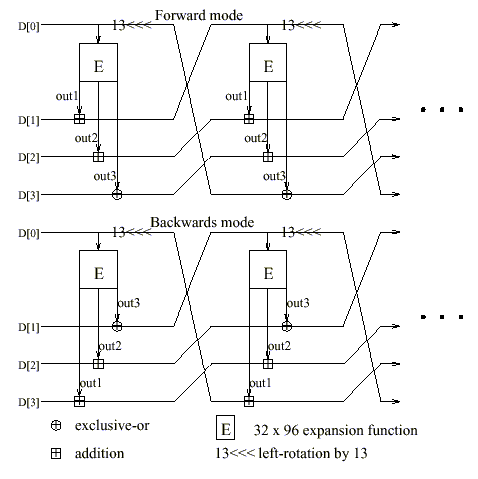
Figure 3: Type-3 Feistel network of the main keyed transformation [MarsIBM99]
The E-function (Figure 4) is a combination of different operations that mix two key word with the input word. This is also the place where the multiplication comes into play. It also contains an S-box lookup. The k' (odd) means that this are special made-up key words with special properties (see Key Expansion ). The E-function is one of the best designed parts of the MARS algorithm. The different functions are combined in a way that maximizes the advantage of each.
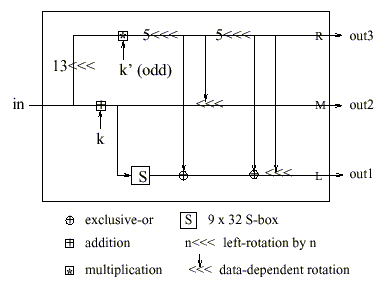
Figure 4: The E-function of the main keyed transformation [MarsIBM99]
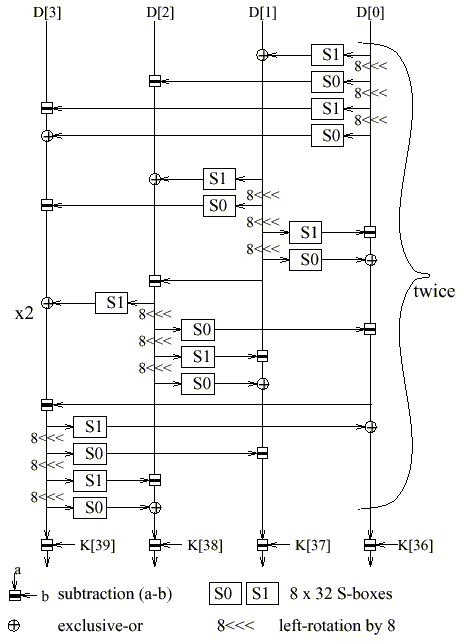
Figure 2: Structure of the forward mixing phase [MarsIBM99]
| [MarsIBM99]
|
C.Burwick, D.Coppersmith, E.D'Avignon, R.Gennaro, S.Halevi, C.Jutla, S.Matyas, L.O'Connor, M.Peyravian, D.Safford, N.Zunic, "MARS - a candidate cipher for AES", IBM Corporation, September 1999. http://www.research.ibm.com/security/mars.pdf or http://csrc.nist.gov/encryption/aes/round2/AESAlgs/MARS/mars.pdf |
| [TweakIBM99] | Shai Halevi, "Detailed discussion of the MARS "tweak" for Round 2", IBM Corporation, Mai 1999. http://csrc.nist.gov/encryption/aes/round2/AESAlgs/MARS/mars-twk.txt |
| [RC6-MIT-RSA]
|
Ronald L. Rivest, M.J.B. Robshaw, R. Sidney, Y.L. Yin, "The RC6 Block Cipher", M.I.T. Laboratory for Computer Science,RSA Laboratories, http://csrc.nist.gov/encryption/aes/round2/AESAlgs/RC6/cipher.pdf |
| [Rijndael99]
|
Joan Daemen, Vincent Rijmen, "AES Proposal: Rijndael", Proton World Int.l, Belgium, Katholieke Universiteit Leuven, Belgium, September 1999, http://csrc.nist.gov/encryption/aes/round2/AESAlgs/Rijndael/Rijndael.pdf |
| [Serpent]
|
Ross Anderson, Eli Biham, Lars Knudsen, "Serpent: A Proposal for the Advanced Encryption Standard", Cambridge University, England; Technion, Haifa, Israel; University of Bergen, Norway; http://csrc.nist.gov/encryption/aes/round2/AESAlgs/Serpent/Serpent.pdf |
| [Twofish]
|
Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson, "Two sh: A 128-Bit Block Cipher", Counterpane Systems, University of California Berkeley, http://csrc.nist.gov/encryption/aes/round2/AESAlgs/Twofish/Twofish.pdf |